1.9 KiB
1.9 KiB
Lab 3
Prep
- Gitea set up
- MFA set up
- Add git ignore
- Secrets/Token Management
- Consider secret-scanning
- Added git-leaks on pre-commit hook
- Consider secret-scanning
- Create & Connect to a Git*** repository
- Modify and make a second commit
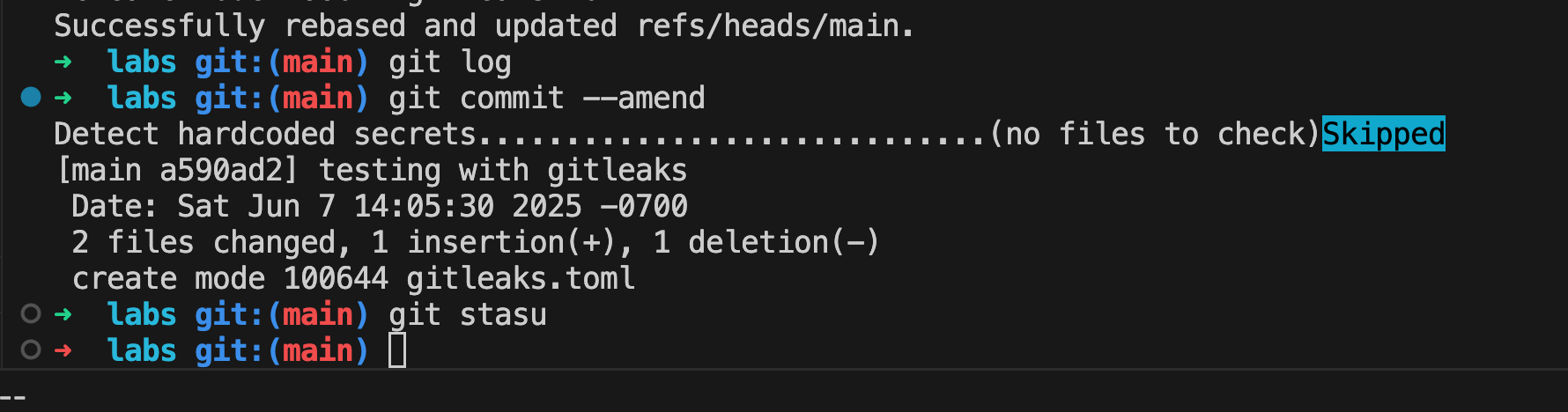
- Test to see if gitea actions works
- Have an existing s3 bucket
Resources
- Capital One Data Breach
- Grant IAM User Access to Only One S3 Bucket
- IAM Bucket Policies
- Dumping S3 Buckets!
Lab
- create a custom IAM Policy
- create an IAM Role for EC2
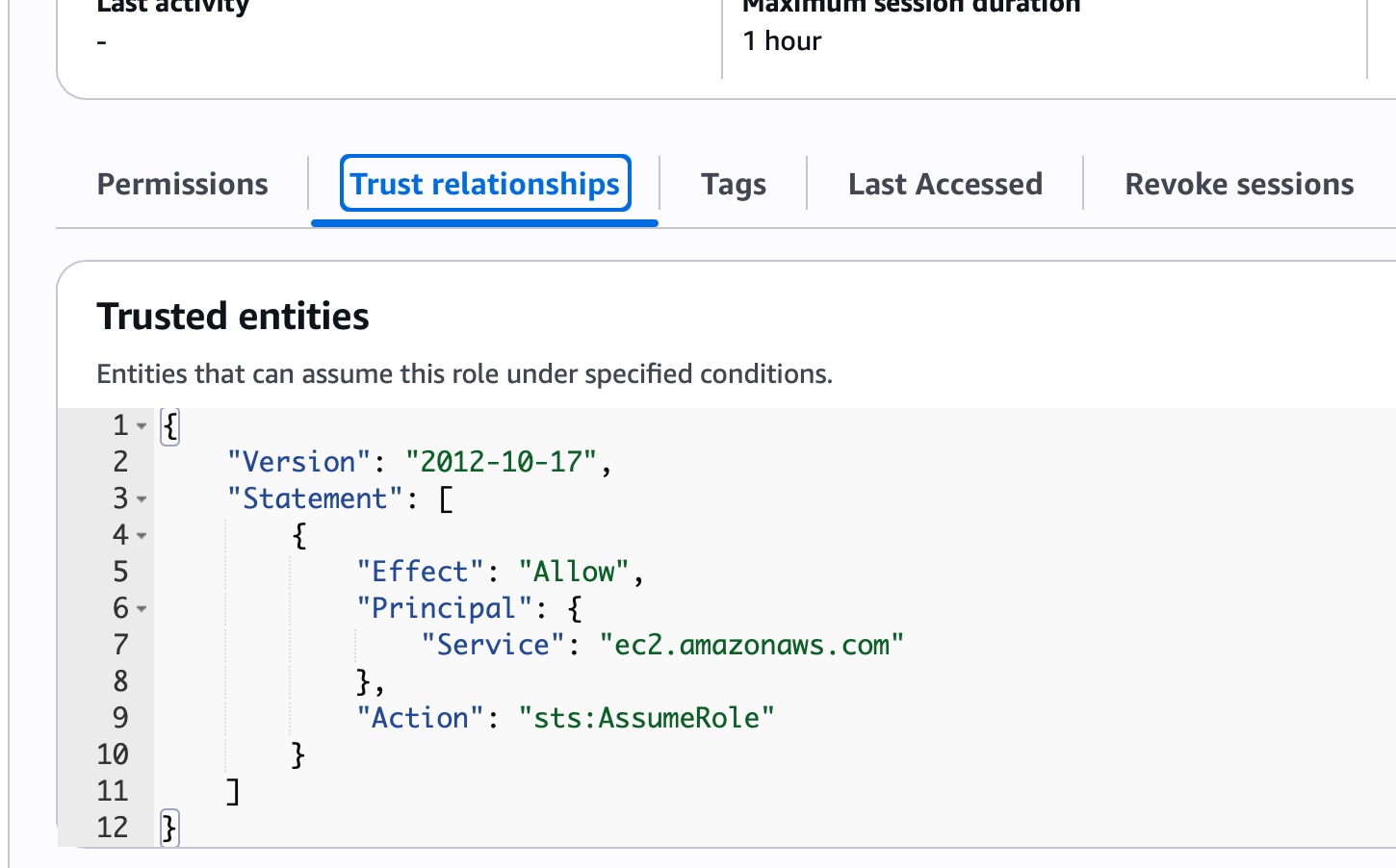
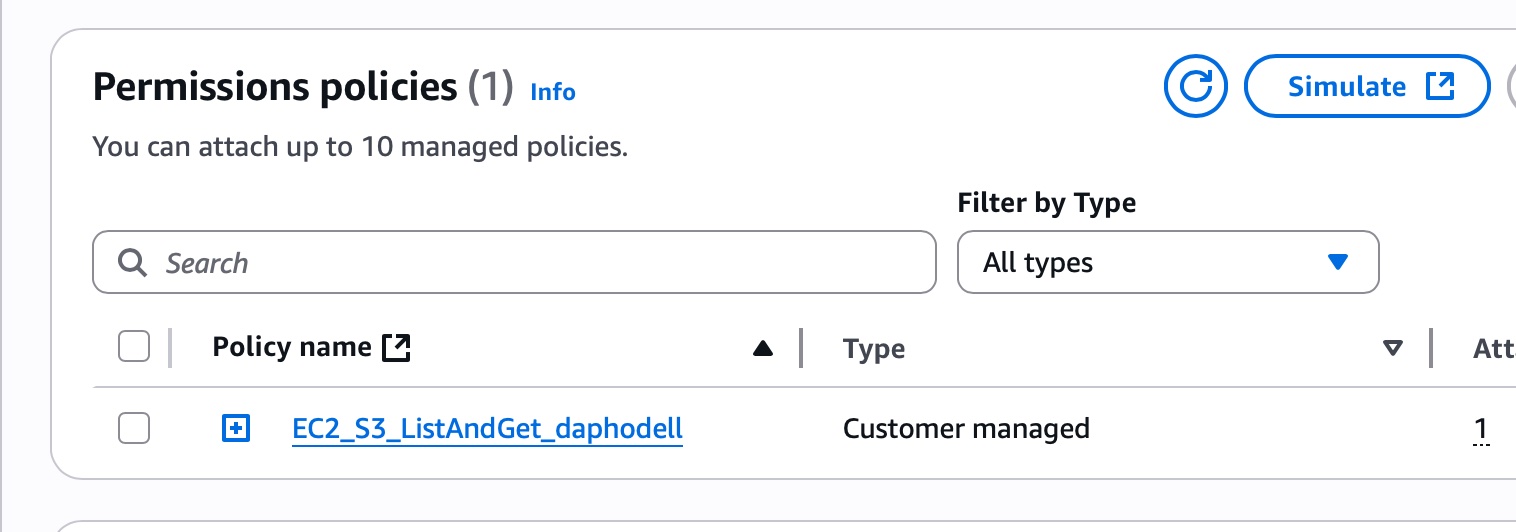
- Attach the Role to your EC2 Instance
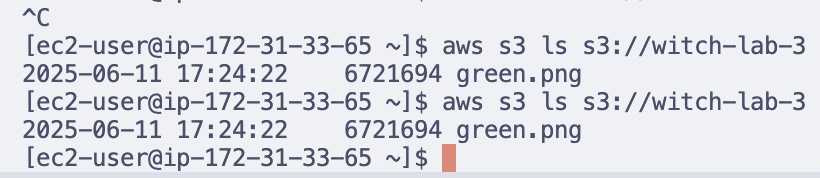
- Verify is3 access from the EC2 Instance
Stretch
- Create a bucket policy that blocks all public access but allows your IAM role
Terms
Identity Access Management
graph LR
IAMPolicy -- attaches to --> IAMIdentity
ExplainIAMIdentity[users, groups of users, roles, AWS resources]:::aside
ExplainIAMIdentity -.-> IAMIdentity
classDef aside fill:#fffbe6,stroke:#bbb,stroke-dasharray: 5 5,stroke-width:2px;
End lab
- Clean up
- Custom roles
- Custom policies
- Stop ec2 Instance
- Remove s3 bucket